Principles of cryptography
In symmetric cryptography sender and receiver share a secret key. AES and DES are two Data Encryption Standards.
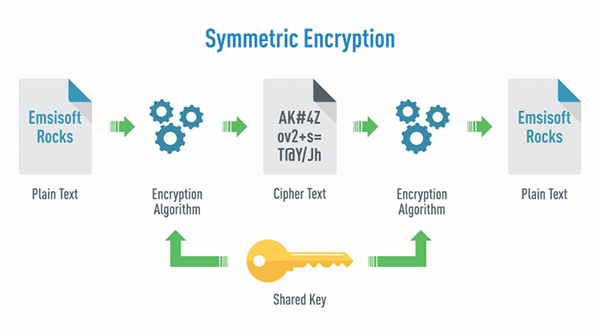
Figure 35 Symmetric Encryption schema
Симметрик түлхүүрийн шифрлэлт by Munkhzaya Ganbold (Own work) from Wikipedia CC BY-SA 4.0
Public key cryptography (asymmetric encryption) is a radically different approach. Sender and receiver do not share secret key. Public encryption key known to all. Private decryption key known only to receiver.

Figure 36 Asymmetric Encryption schema
Simplified illustration of asymmetric/public key encryption... by Fleshgrinder and
The People from The Tango! Desktop Project... (Own work) from Wikipedia Public Domain
The sender needs the receiver’s Public Key. The receiver owns a secret Private Key such that given the public key it should be impossible to compute private key. RSA (Rivest-Shamir-Adleman) algorithm was developed in 1977, and it is the most used public key cryptographic system.
However, RSA is computationally intensive. DES is at leas 100 times faster than RSA. In practice, we use public key crypto to establish secure connection, then establish second key symmetric session key for encrypting data. In the example, Bob and Alice use RSA to exchange a symmetric key Ks. Once both have Ks, they use symmetric key cryptography.





