Implementation of digital signature
It is computationally expensive to public-key-encrypt long messages. The goal is to have a fixed-length, easy to compute digital “fingerprint”, and then to apply hash function H to m, get fixed size message digest, H(m). MD5 and SHA-1 are hash functions widely used.
Digital signature is a signed message digest:
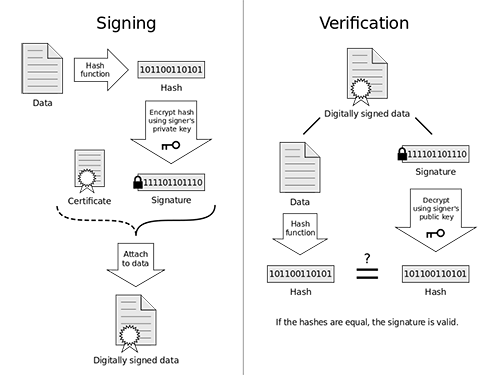
Figure 37 Operation of a digital signature and its verification
Click to enlarge
Diagram illustrating how a simple digital signature is applied and verified by Acdx (Own work) from Wikipedia CC BY-SA 3.0
-
Project
This resource was developed as part of an Erasmus+ project, funded with support from the European Commission under grant agreement 2016-1-SE01-KA203-22064.
The project was a collaboration between:
This resource has been released under Creative Commons license CC-BY-SA 4.0.
Contact
If you would like more information on this resource please contact:
- Academic content – The University of Alcalá (https://www.uah.es/en/)
- Technical resource development – The University of the Highlands and Islands Educational Development Unit - EDU (edu@uhi.ac.uk)
Disclaimer
Except where otherwise noted, this website is licensed under Creative Commons license CC-BY-SA 4.0. All images used under permission remain the copyright of the license holder.
PDF
Download a copy of this resource in PDF format.
You can also print individual pages by printing directly from the browser.
×






